Solodit Checklist Explained (1) : Denial-of-Service Attacks Part 1
Attacker's Mindset / Denial-of-Service Attack
Alright, security seekers! Hans here, ready to dive into our first tasty slice of the "Solodit Checklist Explained" pie!
If you're new to the feast, welcome! This series is all about turning the Solodit smart contract audit checklist – all 380+ items of it! – into something you can actually use. Think of it as turning a daunting quest into a fun treasure hunt, where the hidden gold is robust, secure code. And trust me, there's not much I enjoy more than secure code.
Remember the Preface? We set the stage, promising a journey packed with practical examples and stories from the trenches. We're not just aiming to prevent disasters; we're building confidence – the kind that lets you sleep soundly, knowing your smart contracts aren't ticking time bombs. Because let's be honest, who really sleeps well when they think their code is about to be exploited?
Today, we're wrestling with a well-known topic that lurks in the shadows of nearly every smart contract project. It's one of those sneaky issues that makes security experts facepalm during audits or after contests because it's so common yet so easily overlooked when you're deep in the coding trenches.
I'm talking about Denial-of-Service (DoS) attacks!
We'll be dissecting 3 checklist items:
SOL-AM-DOSA-1: Is the withdrawal pattern followed to prevent denial of service?
SOL-AM-DOSA-2: Is there a minimum transaction amount enforced?
SOL-AM-DOSA-3: How does the protocol handle blacklisting functionality tokens?
So, grab your favorite brain-boosting beverage, buckle up, and let's kick this show into high gear!
Why Worry About DoS Attacks?
Okay, before we dive headfirst into the code's deep end, let's zoom out for a sec. Why should you even care about DoS attacks? I mean, isn't that just a problem for traditional, centralized servers? Something for the big corporations to fret about, right? Wrong!
The truth is, in the world of decentralized finance (DeFi), DoS attacks can be utterly devastating.
Think of this nightmare scenario: your painstakingly crafted staking contract, designed to generously reward your loyal users, suddenly… stops. It grinds to a halt because some malicious actor is flooding it with a transaction tsunami. Users can't withdraw their hard-earned funds, the entire system becomes frustratingly unusable, and your reputation? Well, it takes a nosedive faster than a memecoin after a rug pull (and we all know how that feels).
Yeah, not pretty. Definitely not a situation you want to find yourself in.
DoS attacks are about exploiting vulnerabilities in your code, turning your smart contract unusable, either for specific users or for everyone. They're like digital roadblocks, preventing legitimate folks from accessing your protocol's well-intentioned services! In a space where trust is everything, as valuable as the code itself, a successful DoS attack can be absolutely catastrophic.
To really illustrate this, think of it like this: you've poured your heart and soul into building a beautiful, decentralized coffee shop. It's the best coffee shop in the world. But then someone comes along and keeps ordering thousands of empty cups of coffee, clogging up the entire system and preventing real, paying customers from getting their caffeine fix. Infuriating, right? That's a DoS attack in a nutshell! And you don't want that happening to your DeFi coffee shop.
Denial-of-Service (DOS) Attack: High-Level Overview
Alright, so what exactly are we up against here? We're not talking about hacking into servers or cracking complex encryption. DoS attacks are usually about leveraging design flaws in your smart contract logic. It's not brute force, they are using subtle manipulation to beat you.
Here's the general idea broken down into bite-sized pieces:
Logic Exploitation: This is all about finding clever (or, more accurately, malicious) ways to trigger state changes that lead to reverted transactions or infinite loops, effectively freezing the contract. Sounds like an episode in a Sci-Fi show right?! But it's very real. And it happens more often that you might think. Who knew exploits could be as creative as literature? Some auditors really are smart contract poets.
Resource Exhaustion: Think of this like the tragedy of the commons, but with gas fees. It occurs when the attacker floods the contract with requests, consuming excessive gas and making it prohibitively expensive for legitimate users. Remember, every action on the blockchain costs gas, and a flood of transactions can drive those costs through the roof.
Now that we've briefly covered the high-level view (and hopefully convinced you that DoS attacks are a real threat), let's plunge into some concrete ways to mitigate these potential headaches.
SOL-AM-DOSA-1: Is the withdrawal pattern followed to prevent denial of service?
Translation: Are you using the "pull" instead of "push" pattern for withdrawals?
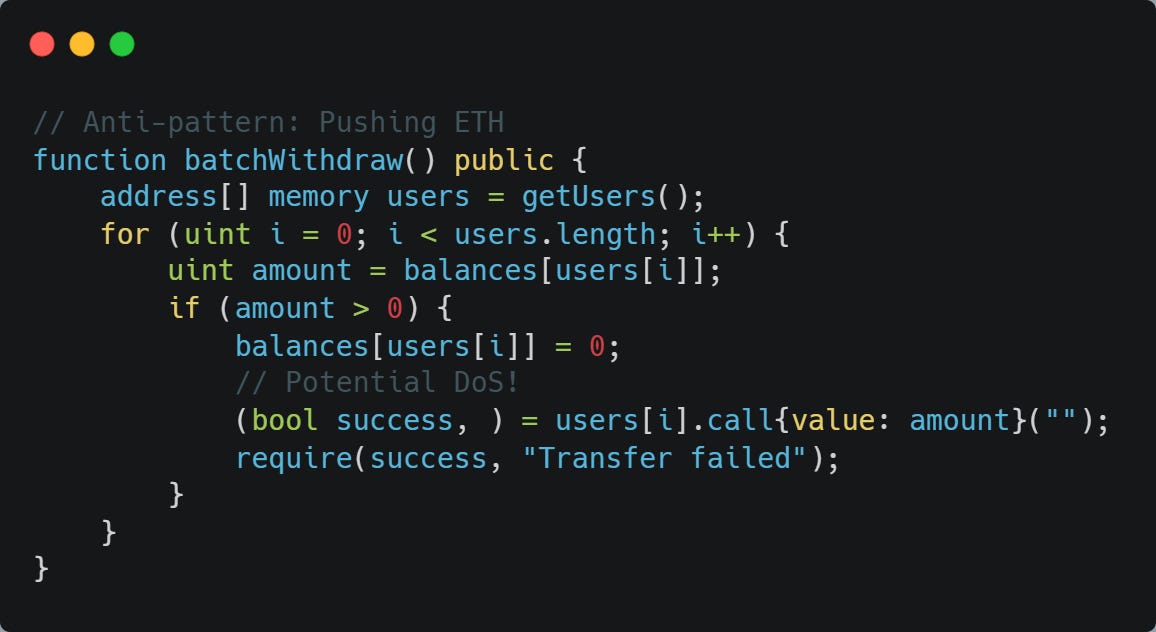
This is an absolutely crucial one, folks! I cannot scream this enough. The classic mistake (and one I've definitely seen way too many times in audit contests) is to push ETH to users in a withdrawal function. Seems simple enough, right? Dead wrong! Let's check out some code:
Why is this so bad? Let me spell it out.
If any of users[i] is a contract that reverts on receiving ETH (for whatever reason – maybe they're malicious), the entire withdraw function will revert for everyone! One bad apple really can spoil the whole bunch here. This creates a real Denial-of-Service (DoS) situation, as legitimate users are unable to withdraw funds because of a single failing address. Imagine the chaos!
The Fix: The Pull Pattern, Your New Best Friend
Instead of pushing, let users pull their tokens. They initiate the transfer from the contract. It's like giving them the key to the vault.
Now, if a user's withdrawal fails, it only affects them. The contract continues to function blissfully for everyone else. That's decentralization done right! The require statement checks if the transfer was successful. If unsuccessful, the transaction is reverted only for the requesting user, having a minimal impact on on-going operations.
Real-World Example:
The example provided in the checklist item details a scenario where fees are transferred to the owner before the user's withdrawal. If the owner's address is accidentally set to the zero address, or if the owner is, ahem, a mischievous contract that reverts on token transfer, user withdrawals will fail. Ouch. That's a nasty one to debug! The minimal example and PoC written in Foundry are available here.
Checklist Power: Simply asking, "Are we using the pull pattern?" during a code review could have flagged this DoS vulnerability before it went live. Prevention is always better (and cheaper!) than cure. Think of it as saving a trip to the DeFi emergency room.
SOL-AM-DOSA-2: Is there a minimum transaction amount enforced?
Imagine this: You're running a store and, for some reason, you happily accept individual pennies. An attacker, or a neighborhood kid with a summer prank in mind, decides to pay for everything with individual pennies, one at a time. That would slow down service and annoy your actual customers!
Think about how that would affect your gas on the blockchain.
Translation: Are you preventing "dust" transactions (tiny, insignificant amounts) from clogging up your contract and making everything miserable?
This one's all about preventing spam, plain and simple. If your contract allows users to interact with it for any amount (even tiny, insignificant fractions of tokens), attackers can flood it with countless zero-value or near-zero-value transactions. All these transactions take up gas and make legitimate operations far more expensive. This increased cost can potentially reach the block gas limit. If that happens, legitimate users wouldn't be able to interact with your beloved protocol anymore.
The Fix: Enforce a Minimum (Be a Bouncer!)
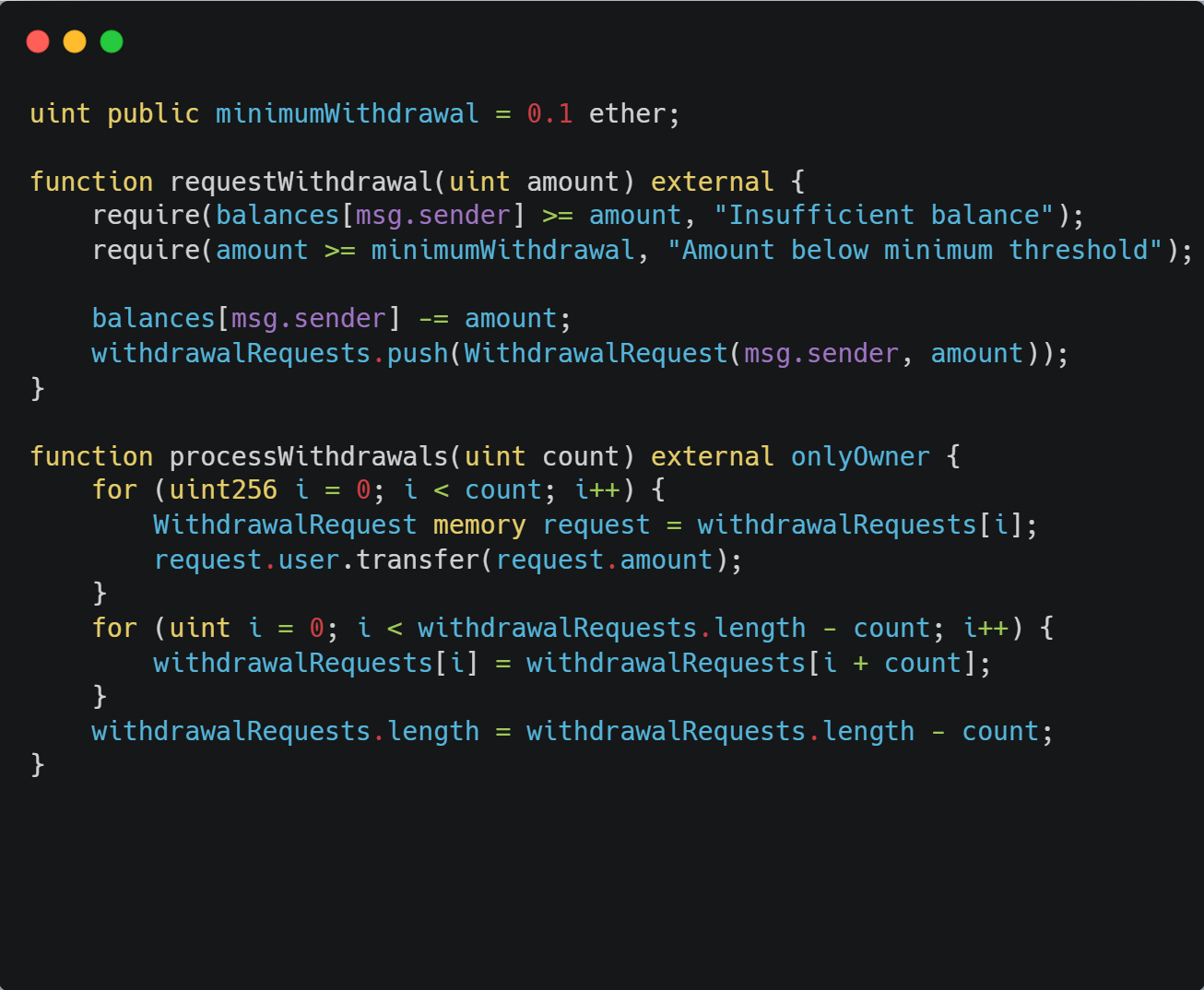
A simple require statement can improve a lot here. Enforce a threshold with a require statement and act like a bouncer checking an ID.
We also need to make it possible to handle the withdrawal requests in batches.
Real-World Example:
The checklist example highlights a contract where users can request withdrawals of literally any amount (even zero), no matter how small. An attacker could exploit this to create a huge queue of zero-value withdrawal requests. This makes processing legitimate withdrawals prohibitively expensive (DoS), costing legitimate users a whole lot of gas. The minimal example and PoC written in Foundry are available here.
Checklist Power: The simple question "Is there a minimum transaction amount enforced?" forces you to stop, think about this specific attack vector, and implement pretty straightforward safeguards. Small changes can make a big difference in your code just with some small effort.
SOL-AM-DOSA-3: How does the protocol handle blacklisting functionality tokens?
Ever been on a "Do Not Fly" list? In traditional systems, that's bad news for travels, but in Web3, it can be devastating!
Translation: Are you considering the implications of using tokens (looking at you, USDC and similar) that can blacklist addresses?
This is a far more nuanced issue, super important in today's evolving world of regulated stablecoins. Some tokens (not naming any names, but cough USDT cough USDC cough) have blacklisting capabilities baked right in. This means a central authority can freeze or outright block specific addresses from using the token.
Why is this a potential DoS timebomb?
Picture a community staking contract where friends, family members, or investment partners pool their tokens together in a "staking group." Sounds cooperative and efficient, right? Each member gets assigned a percentage of the rewards based on their contribution.
But here's where things get dangerously interesting: What happens if just one member of your staking group gets blacklisted by the token contract? Perhaps your cousin ended up on some regulatory watchlist, or your friend's address was flagged due to some completely unrelated transaction. No big deal for the rest of the group, right? Wrong! When your group tries to withdraw its rewards, the entire transaction fails spectacularly! Why? Because the contract attempts to distribute rewards to all members in a single transaction. If one transfer fails, the entire operation reverts! Your group's combined 100 ETH worth of tokens? Completely locked! Your planned withdrawals? Impossible! All because of one member's blacklisting that might have nothing to do with your staking activity!
Even worse? There's typically no way to remove the blacklisted member or redistribute the shares. The group's funds are effectively frozen until the token's blacklist is updated - something that might never happen if the blacklisting was for regulatory reasons.
This isn't some theoretical concern - it's happening in real contracts today! A single point of failure affecting multiple users simultaneously. A collective punishment mechanism that nobody asked for!
Scary, isn't it?
The Fix: Account for Blacklisting. It depends on your tolerance.
There's no single "right" answer here, unfortunately. Each situation is so specific. It really depends on your protocol's design, risk tolerance, and even your legal agreements with users. At least, keep this kind of possibility in mind and design a fallback mechanism while ensuring regulatory compliance.
Checklist Power: This checklist item forces you to think critically about external dependencies and their potential impact on your protocol's core functionality. It's really about anticipating the worst-case scenarios and having at least some kind of plan in place.
The minimal example and PoC written in Foundry are available here.
Wrapping It Up
Denial-of-Service (DoS) Attack: An attack that attempts to disrupt or make a smart contract or its functions unavailable to legitimate users. This can be achieved through various methods, such as consuming excessive gas, causing contract reverts, or exploiting vulnerabilities to block critical operations.
Withdrawal Pattern: A secure smart contract design pattern that emphasizes a "pull" model for withdrawals. Instead of a contract pushing tokens to users, users initiate the withdrawal process, mitigating potential issues like DoS vulnerabilities caused by failing recipient transfers.
Dust Transactions: Extremely small value transactions, often used maliciously to clog a network or smart contract, making legitimate transactions more expensive or hindering their processing.
Token Blacklisting: A feature implemented by some token contracts (e.g., certain ERC20 implementations) that allows specific addresses to be blocked from transferring tokens, effectively freezing their funds or preventing them from interacting with the token.
Examples are available on GitHub solodit-checklist-blog-examples!
Alright, my friends, we have officially conquered three crucial checklist items related to Denial-of-Service attacks! Take a moment to pat yourself on the back. We talked about the pull pattern (embracing user control!), minimum transaction amounts (being a good bouncer!), and the potential minefield of token blacklisting (knowing your dependencies!). Remember, security isn't just about finding bugs; it's about building resilient systems that can withstand unexpected events and malicious actors.
By actively considering these checklist items during your development process, you're not just writing code; you're crafting a safer, more secure, and more trustworthy DeFi ecosystem. And that, my friends, is something truly worth striving for! Trust and transparency are your most valuable assets.
Now, go forth and build something amazing! And hey, don't forget to consult that trusty Solodit checklist. It's not as magical as a unicorn, sure, but it IS your treasure map to building secure smart contracts. Keep learning, keep building, and most importantly, keep those contracts safe!
Stay tuned for the next installment, where we'll continue our thrilling journey! And hey, if you found this helpful, feel free to share it with your fellow code warriors. Let's make the DeFi space a safer place, one checklist item at a time!






Excellent analysis Hans!🙌